What Is a Botnet Attack – Detection and Protection Tips
What Is a Botnet Attack?
Botnet attacks are a grave kind of cyber attack. A botnet is a group of computers that have been compromised by malware and can be used by certain people to carry out attacks on various websites.
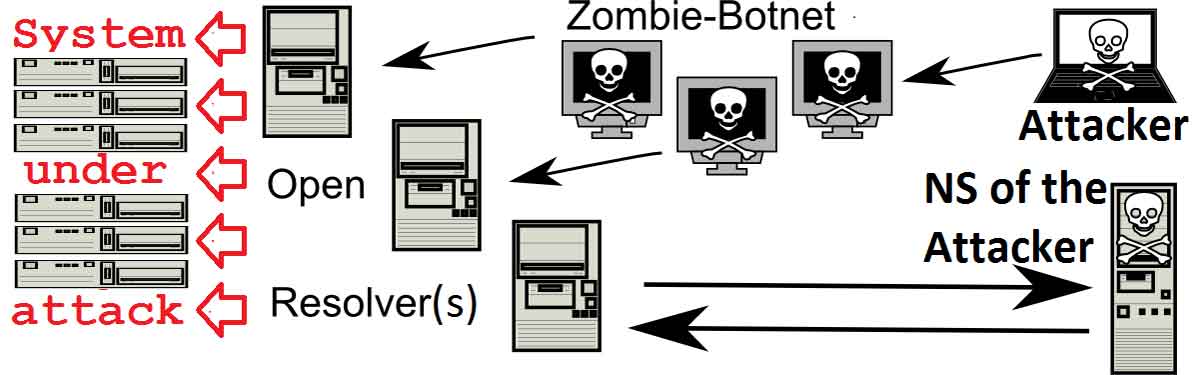
Since we are living in the digital age, it is as important as ever before to take cybersecurity seriously. Security risks are becoming more and more dangerous every day as the internet develops and changes. It is still possible for computer programs to be written that can automatically penetrate computers and then use them for certain tasks without the consent or knowledge of their owner.
How will you know that you have fallen victim to a botnet attack?
Symptoms of a botnet attack
Botnet attacks can be hard to detect because most bots are designed not to draw attention. However, there are certain signs that you will see if your computer is infected with a bot or has been recruited into a botnet:
1. Your computer is acting slowly, but you can’t find out why.
2.
3. You find that programs on your computer are running without your consent (e.g., when you restart your computer, the PC becomes very slow).
4. Your anti-virus can’t detect any viruses on your computer.
How does a botnet attack work?
To understand how botnets function, it is necessary to have a basic understanding of malware and malware infecting practices. Malware stands for “malicious software” and refers to any program written intending to harm a computer. Malware can be divided into different categories according to their function, for example by their type or by the actions they perform.
One important category is known as trojans. Trojans are often described as “a program that does something harmful but disguised as something good”. This means that you will not realize that your computer is infected with a trojan until it is too late. Trojans are dangerous because they usually require a certain action from a user before they can activate and do something bad.
Botnet Malware
With botnets, the “something harmful” that trojans will do is infect your computer with malware without you knowing about it. If your computer is infected with a trojan, then the person controlling the botnet can activate that malware whenever they want and use your computer to carry out their tasks.
Steps to take after a botnet attack
Contrary to what you might think, botnets do not need to be extremely powerful for them to be effective. To indicate how they work and the damage they can do, it is sufficient to say that a single computer infected by malware can be used as part of a botnet without the user being aware.
How to fix a botnet attack?
However, the most important thing is not to panic after you discover that your computer has been compromised. So, what are the steps to take?
1. Reset your computer
If you have recently connected to the internet, then you might have downloaded some malware without knowing it. Using a factory reset will ensure that any viruses are removed from your computer and can no longer do harm.
2. Change your passwords
Your passwords have likely been compromised, so it is necessary to change them immediately, especially if they are the same as the ones you use on your email or social media accounts. If any of those passwords have been used to access some important information, then it might be a good idea to change that password too, just in case.
3. Update your computer
4. Get a new anti-virus
Anti-viruses might not be able to detect all malware and they also need to be updated regularly as well. To keep your computer as safe as possible, it would probably be best to purchase a new anti-virus which you can update as often as you need.
5. Contact your ISP
Even though your computer might have been compromised, the source of the attack was likely another computer on the same network as yours. Here, you should notify your internet service provider immediately so that they can investigate the problem.
6. Get a new ISP
If you think that your internet service might have been compromised, it is best to switch ISPs altogether if you can. Here, a new internet service provider will guarantee your safety because they will not be connected to any of the computers from which you received malware before getting the new connection.
7. Restrict access to the internet
The best way to limit the amount of harm by a botnet attack is to restrict your access to the internet. To do this, you should not allow any unknown devices to connect to your router and also change all of your passwords for each service you use.
8. Monitor your devices
Unfortunately, the kinds of things that malware can do when they are in control of a computer might not be limited to just collecting information about you. This means that it is good practice to monitor all the devices connected to your network after a botnet attack just in case something goes wrong or some device is trying to connect to your network when it shouldn’t.
9. Conduct data backup
Losing all the data that you have gathered over time can be very stressful and this might even cost you money. To avoid losing your information, it is good practice to conduct regular backups just in case something unforeseen happens.
It is always better not to allow botnet attacks to happen. To protect yourself from it, consider choosing an advanced botnet attack protection software. However, if the attack has already happened, there is always a period where everything seems to go wrong and people might become afraid of using their computers. If you follow the steps mentioned above, then you should be able to quickly recover from your botnet attack and get back all the information that was lost.




